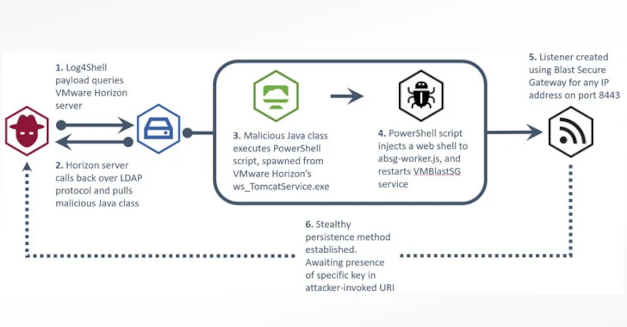
The digital security team at the U.K. National Health Service (NHS) has raised the alarm on active exploitation of Log4Shell vulnerabilities in unpatched VMware Horizon servers by an unknown threat actor to drop malicious web shells and establish persistence on affected networks for follow-on attacks.
The attack likely consists of a reconnaissance phase, where the attacker uses the Java Naming and Directory InterfaceTM (JNDI) via Log4Shell payloads to call back to malicious infrastructure, the non-departmental public body said in an alert. Once a weakness has been identified, the attack then uses the Lightweight Directory Access Protocol (LDAP) to retrieve and execute a malicious Java class file that injects a web shell into the VM Blast Secure Gateway service.